How to spot a phishing email is a science that all must know. With most of our time spent on the internet both for work and leisure, it is important that we be careful of online predators.
Here are some ways in which we can spot phishing emails:
HOW TO SPOT A PHISHING EMAIL – RED HERRING 1 – IS THE EMAIL ADDRESSED TO YOU?
Phishing emails are usually not addressed to you directly. The person sending such emails sends emails to hundreds of thousands of people – he is casting a wide net for his fishing (sorry, phishing expedition). He needs only a handful of fish to bite the bait. Usually, the email that you receive would have “undisclosed-recipients” as mentioned against To: as shown below
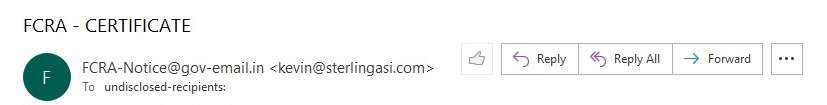
The person sending the phishing email essentially makes a distribution list and sends the email to all within that list. He does not want the email recipients to know who else has been sent that same email.
The To: field therefore reads – undisclosed-recipients.
One caution that I'd like to add here is that there are time when the email sender is able to use an email service or an email client that lets him send emails individually to recipients. In that case it may appear that the email is addressed to you personally. Therefore, it would be prudent to be careful and look for the other ways to spot phishing emails as mentioned below.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 2 – IS THE EMAIL SENT FROM A PUBLIC DOMAIN?
Many a times the email sender claims to belong to a company or bank or a reputed organization such as IMF or UN. However, the mail is sent using a email service such as Gmail or Yahoo. An example is shown below:
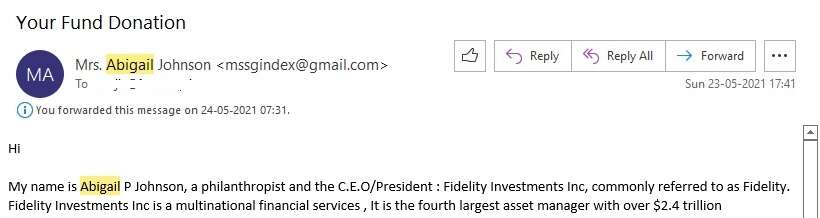
Why would a person who claims to be the CEO of an organization such as Fidelity Investments send such an important and official email from a GMAIL address? The email should have been sent from a domain such as ‘fidelity.com'. Such an email is definitely a phishing email.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 3 – IS THE REPLY TO EMAIL ADDRESS SAME AS FROM EMAIL ADDRESS ?
In case of most phishing emails, the “reply to” email address is different compared to the email address from which it was received as shown below:
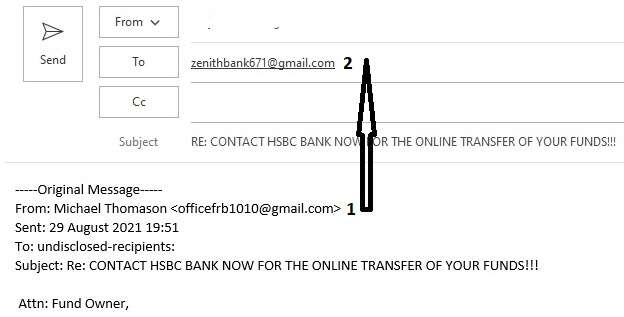
The email has been sent from “officefrb1010@gmail.com”. However as soon as I clicked on the reply button, the reply to email address is can be seen as “zenithbank671@gmail.com”.
Who does that?
Also, as you can see, the email is addressed to “undisclosed -recipients”, supposedly from HSBC bank and uses GMAIL address. And the reply to email address is different from the originating email address. A classic phishing email. Now you know how to spot a phishing email!
HOW TO SPOT A PHISHING EMAIL – RED HERRING 4 – SUSPISCIOUS FROM EMAIL ADDRESS
The Red Herring 2 discussed above if the email had been sent from a Public email service such as GMAIL.
There are other ways too in which the from email address could be fraud. You must cross-check the email domain on any suspicious email. The domain is the name after the @ symbol in the email address. If the email is not sent from a public email service such as GMAIL or YAHOO, the sender might try to show as if it is being sent from the Company domain. In that case it should match the name and company of the attempted sender (be on the lookout for minor misspellings!). If you are unsure, try looking up the company’s domain through a search engine.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 5 – PERSON FROM ONE COUNTRY SENDING EMAIL FROM ANOTHER COUNTRY DOMAIN
Many times you'd find that the email sender claims that he lives in country X yet the email domain belongs to county Y. An example is shown below:
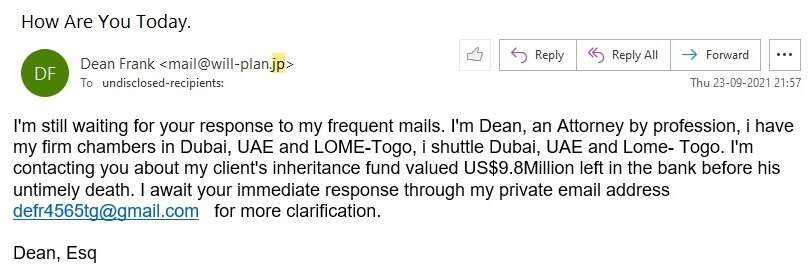
The sender claims that he lives in Dubai, UAE and Togo. However, the email domain refers to Japan!
You can find the list of country specific domain extensions here.
This email fulfills all the above red herrings. One has to be really naïve to fall for such a phishing email.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 6 – INCORRECT SPELLINGS AND BAD GRAMMER
More often than not, the phishing email sender gives himself away with use of incorrect spellings and bad grammar. If you receive an email with obviously bad grammar and many wrong spellings, assume the worst.
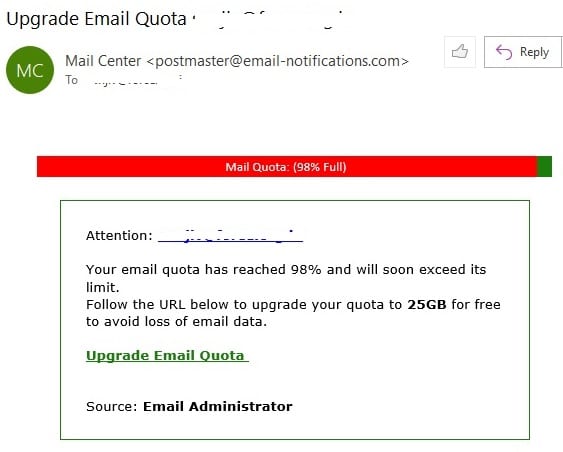
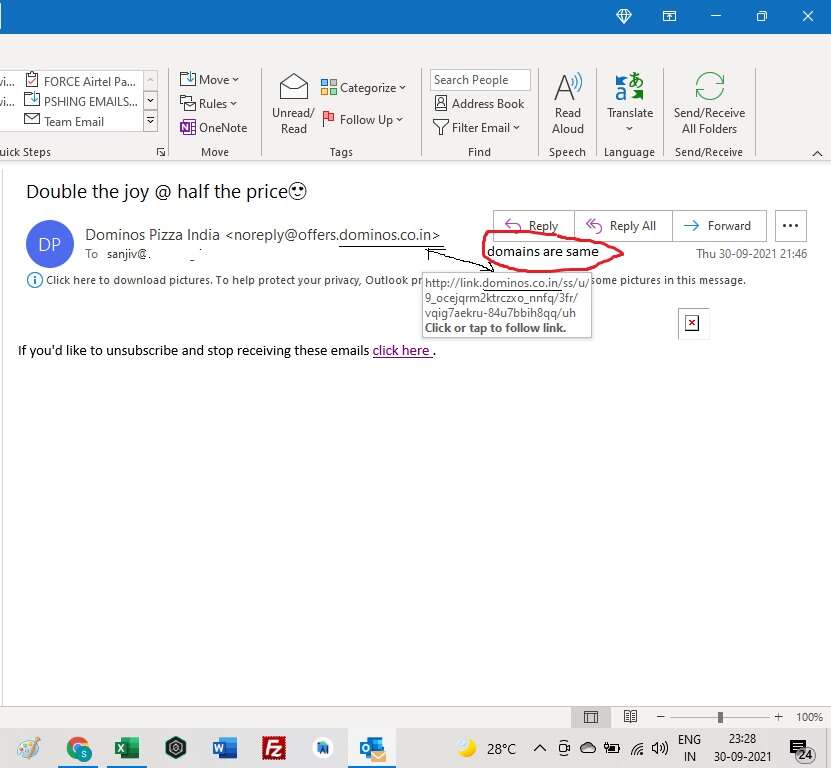
HOW TO SPOT A PHISHING EMAIL – RED HERRING 7 – DISHONEST HYPERLINKS
When an email has links, carefully examine the hyperlinks. They contain the address of the web page where you will be taken once you click on it.
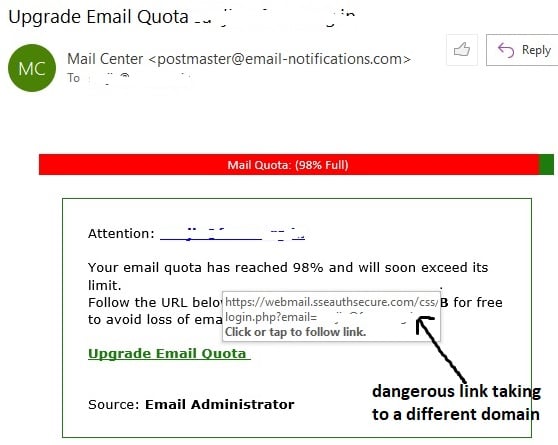
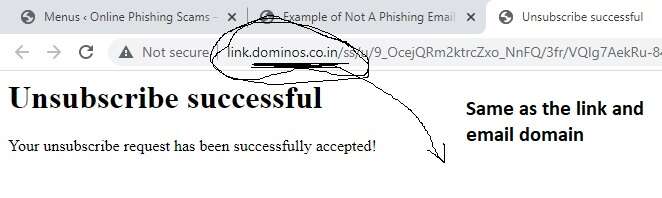
To examine the hyperlink, take the cursor on the link. It will show you the address of the webspage as shown below:
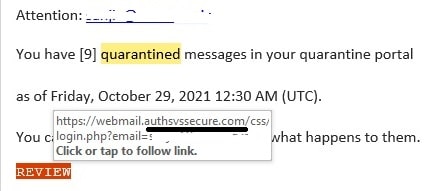
The underlined link shows the domain where the link will take you, if you click the link in this email. In this case, the website in the link is different from the website where I would have expected to be taken based on the sender's claim.
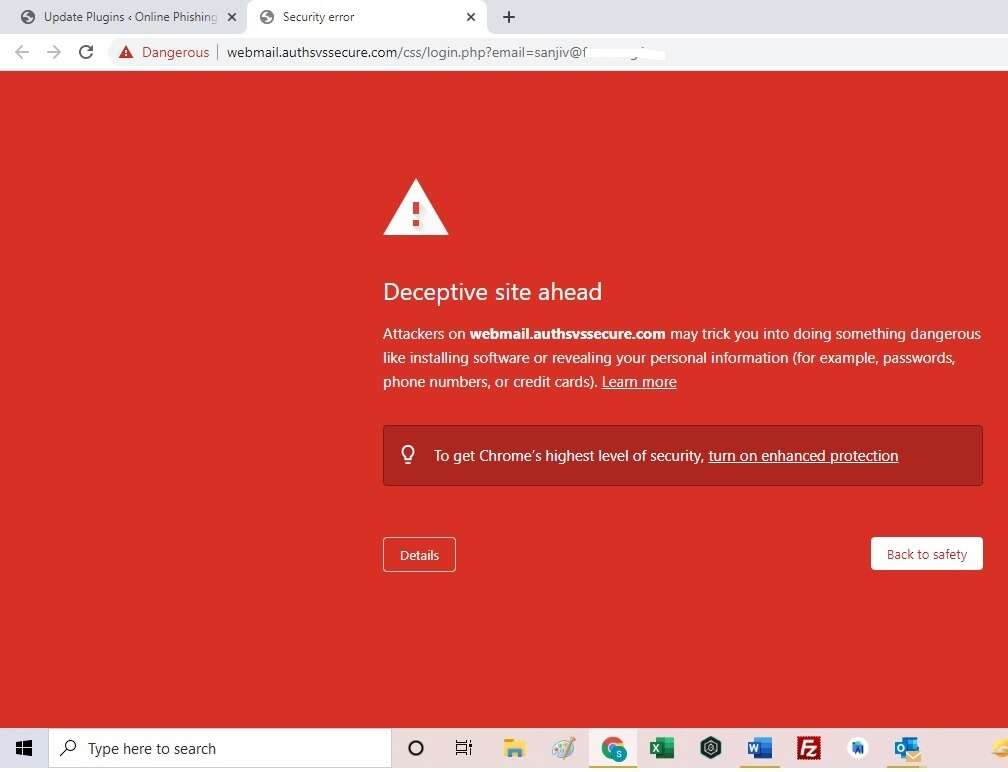
This is a 100% scam link. The objective of the email sender is to infect the copmputer of the recepient with virus or malware.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 8 – QUESTIONABLE ATTACHMENTS
One of the Golden Rules of online secure behaviour is – do NOT open any attachments until you are 100% sure that the sender is legitimate. Many a times one receives an email from a total stranger with attachments. An example is shown below
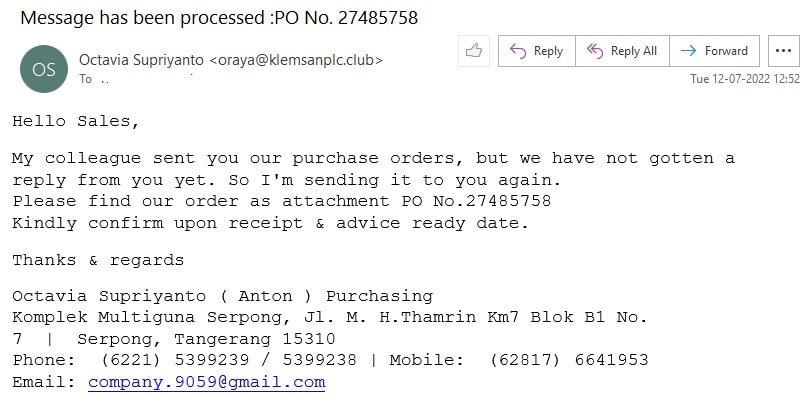
I have absolutely no idea about what order he is talking about. The attachment 100 percent contains virus. That is why the anti virus I use on my laptop deleted the attachment.
If you do not know the sender and the email has attachment that you find strange, you can be reasonably sure that it is phishy. Do not open it if you have no protection on your device.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 9 – SENSE OF URGENCY
There are emails from unknown senders that ask you to respond urgently. The sender could use reward or scare or threat to get you to respond faster or click on a link. An example is given below:
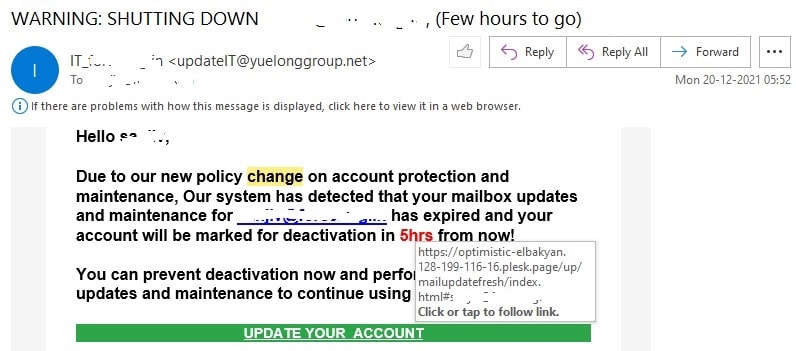
The sender would like me to click on the hyperlink in the email NOW else according to him my email service will be blocked.
Such urget action emails are to be ignored. They are scam emails and one must not fall victim to them.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 10 – REQUEST FOR SHARING PERSONAL INFORMATION
No company, bank, government department, agency – No one – will ask for sensitive or personal information over email. If any credit card information, social security number, driving license or passport details etc., are requested, do not share them. Not over email. If you think that you might be missing out on something call the customer support number of the organization to validate. And yes, look up the phone number yourself. Do not call any phone numbers given in the email that you received.
HOW TO SPOT A PHISHING EMAIL – RED HERRING 11 – EMAIL SENT AFTER OFFICE HOURS OR ON NON-WORKING DAYS
View with caution any email that seem to have been sent outside of business hours or on a holiday. Why would a bank executive send you an email at 10 pm or on a Sunday?
This may not be an exhaustive list of pointers on how to spot a phishing email. If you have more suggestions, please do share. I also look forward to your comments on how to make our online presence more secure.
Please do use the comment box below.