News & Resources
Sextortion Email: Overdue Payment
Today, I received a sextortion email from someone who claimed many frightening things - frightening, if true. I am, however not scared because I know that what he has written in the email is a pack of lies. Let us go through the sextortion email and my comments in red...
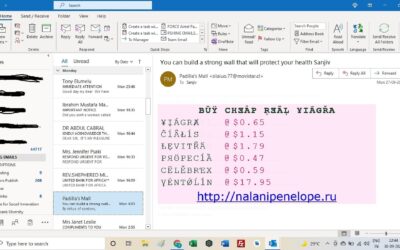
Viagra Spam Email
To exploit the sexual fantasies of people viagra spam email is flooding email boxes around the world. These emails always contain dangerous links in their body or accompanying images. These fraudulent emails are quite obviously scams and should not be opened if...
Abigail Johnson: Your Fund Donation
I received an email from someone who claimed to be Mrs. Abigail Johnson. She introduced herself as a philanthropist and the C.E.O/President of Fidelity Investments Inc, commonly referred to as Fidelity. She told me that I should count myself as lucky to have been ...
Internet Security Audit: Do-It-Yourself Guide
Need for Internet Security With the increase in our online presence, comes the need for internet security audit as we become more vulnerable to online frauds. Just as we try and keep our homes safe by ensuring that security measures such as locks, alarms, gates and...
Mrs Rose James: Funds for Lord's Work
About a year back, I had received an email from one Mrs. Rose James offering me 17.5 Million US Dollars for Lord's work! Below, you'll find my communication with her. My comments are in red. The email from Mrs. Rose James From: Mrs.Rose james <www.@docomonet.jp>...
How To Spot A Phishing Email
How to spot a phishing email is a science that all must know. With most of our time spent on the internet both for work and leisure, it is important that we be careful of online predators. Here are some ways in which we can spot phishing emails: HOW TO SPOT A PHISHING...
Phishing Email: Understanding Modus Operandi
I believe there exists no email address that does not receive any phishing email. It may be a different thing that a phishing email may not get delivered to an email id because of a secure perimeter. However, if an email address exists then there is a sure shot...