Business VPN As a Service – Perimeter 81
Last week we talked about Perimeter 81 – a world class Business VPN As a Service. Let us now discuss more about the VPN service – Perimeter 81
Getting Started with the Perimeter 81 – Business VPN as a Service
With Perimeter 81’s zero-touch framework, it’s very simple for IT managers to begin working with the product and roll out networks in a matter of minutes. First, you sign on to the cloud management platform to create a dedicated workspace. This provides your organization with its own distinct URL where your team can build and manage your network.
Within the cloud management platform, you can easily purchase licenses for team members and private gateways by attaching credit card details, or using PayPal, and selecting the desired license amount for VPN as a service. The deployment of a network is fully automated and highly scalable. Team members can join through their organization’s SSO provider, or by email invitation.
Team members receive invitations to download single-click client apps, available for Windows, Mac, iOS, and Android. These applications encrypt device traffic and allow team members to safely access company resources and work securely – whether they’re in the office or on the go.
SWG & Web Filtering: Benefits & Pain Points
A Secure Web gateway (SWG) has become the number one solution in protecting thousands of companies from online dangers. SWG achieves web security with web filtering, web activity tracking and malware protection ‒ a triple web threat.
Through the implementation of SWG, companies can create web filtering rules that control user Internet access for all employees. By tracking user web activity, IT admins can get a granular view of Internet traffic and understand which sites are being accessed by who. On top of that, with malware detection, malicious files are scanned and blocked from user download, preventing security breaches.
Web filtering is the key feature of SWG that allows the admin to determine who can reach what URL or website, even if they are not connected to the network. Users can be allowed access, denied access, or warned against proceeding.
Benefits of Web Filtering
- Filter out malicious sites and protect your employees and network from web-based threats.
- Increase productivity by decreasing distractions from unwanted web sites.
- Prevent shadow IT and ensure that employees are only using authorized sites and web applications for business functions
- Track web activity and increase compliance with web auditing requirements
- Define bypass rules as necessary to comply with user privacy regulations and prevent issues with commonly used web applications
Pain Points that Web Filtering Addresses
- Danger of hacks through phishing attempts of employees or employee access of malicious sites.
- Employee use of distracting or illicit sites (such as gambling sites) during work hours.
- Need to provide auditors with tracked web activity for compliance purposes.
How Web Filtering Works
With Perimeter 81 VPN as a service, admins can set web filter rules using the same easy interface and quick deployment that the Perimeter 81 platform is known for.
With, Perimeter 81, web filtering operates even when the employee is not connected to the network – in other words, the employee device is always protected.
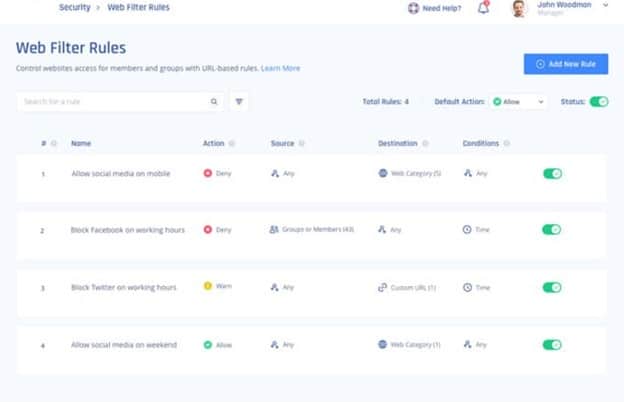
Web Filter Rules
Web filter rules can be set per employee or employee group and can also apply to specific days of the week or times.
Admins can choose to block a specific site or an entire category, such as “Gaming” or “Phishing.” Categories are dynamically updated daily as new sites are identified.
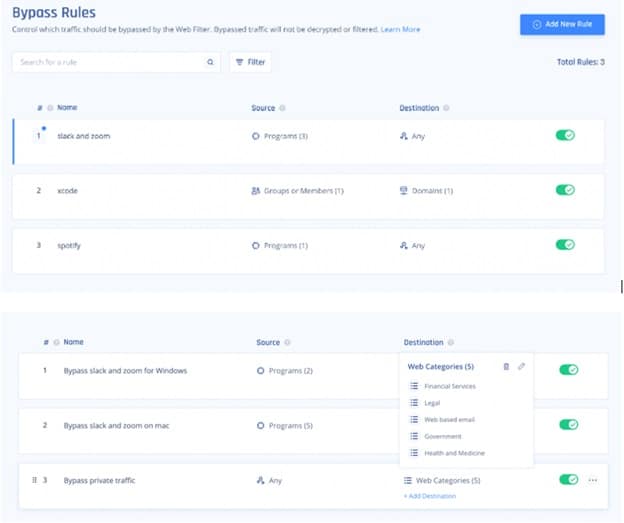
Bypass Rules
There are certain cases when web filter rules should be bypassed.
- If there are privacy regulations – for example, if employee access of healthcare or financial sites is not allowed to be tracked.
- If an application, such as Slack or Dropbox, needs unfiltered access.
For this Perimeter 81 has Bypass Rules, which can be similarly set for specific employee groups, web categories, and programs.
Monitoring and Tracking
Monitoring and tracking are a fundamental and necessary part of SWG.
Perimeter 81 VPN as a service Web Filtering tracks all employee attempted access of “denied” or “warned” sites, so that companies can take action following suspicious activity. Reports can be exported as a CSV file for auditing and analysis purposes.
Perimeter 81 Support
Perimeter 81 VPN as a Service offers 24/7 support with immediate, 1-day email response for any questions. After every customer joins, the Customer Success team reaches out to them to welcome them to the service and provide them with a 1:1 onboarding session. Furthermore, Perimeter 81 has a documentation center which provides helpful product guides, video tutorials and how-tos in order to proactively help our customers with all product features and aspects of the service.
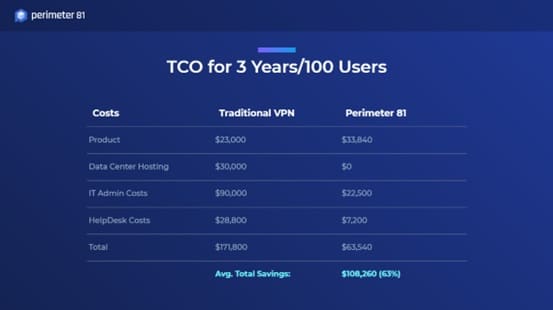
Cost Reducing Proof VS traditional, hardware-based business VPN
Perimeter 81 is a Business VPN as a Service which is extremely cost effective. The Total Cost of Ownership (TCO) of Perimeter 81 is almost one-third of other traditional VPN services.
What is the Pricing of Perimeter 81?
Perimeter 81 offers 3 simple, straightforward, pay-as-you-grow pricing with a 20% discount for annual plans:
- Essentials: $ 8 /mo per user + $4 0/mo per gateway (minimum 5 users)
- Premium: $ 12 /mo per user + $4 0/mo per gateway (minimum 10 users)
- Enterprise: Custom pricing + $4 0/mo per gateway (minimum 50 users)
The service offers a 30-day money-back guarantee to ensure clients are satisfied. Check out the full pricing and plans here
Scheduling A Demo
It is very easy to schedule a demo with the Perimeter 81 team. Simply visit Perimeter 81 demo, provide a few pieces of information and the Perimeter 81 team will provide you with a 1:1 customized demo, explaining how Perimeter 81’s solution can help to address your organization’s network and cloud security needs. They also offer in-site chat support for connecting with a support or sales representative to schedule a demo and learn more.
You can also access Customers’ Case Studies at